Scammers are using invoices and actually sending them through PayPal.com!!!
Basically, the idea is to trick the recipients into calling the number shown to dispute a pending charge. (See pic below). These emails actually do come from Paypal.com and include a link at Paypal.com that displays the actual invoice for the supposed transaction.
Typically, the invoice will say that the user’s account is about to be charged hundreds of dollars. Recipients who call the supplied toll-free number to contest the transaction are soon asked to download software that lets the scammers assume remote control over their computer.
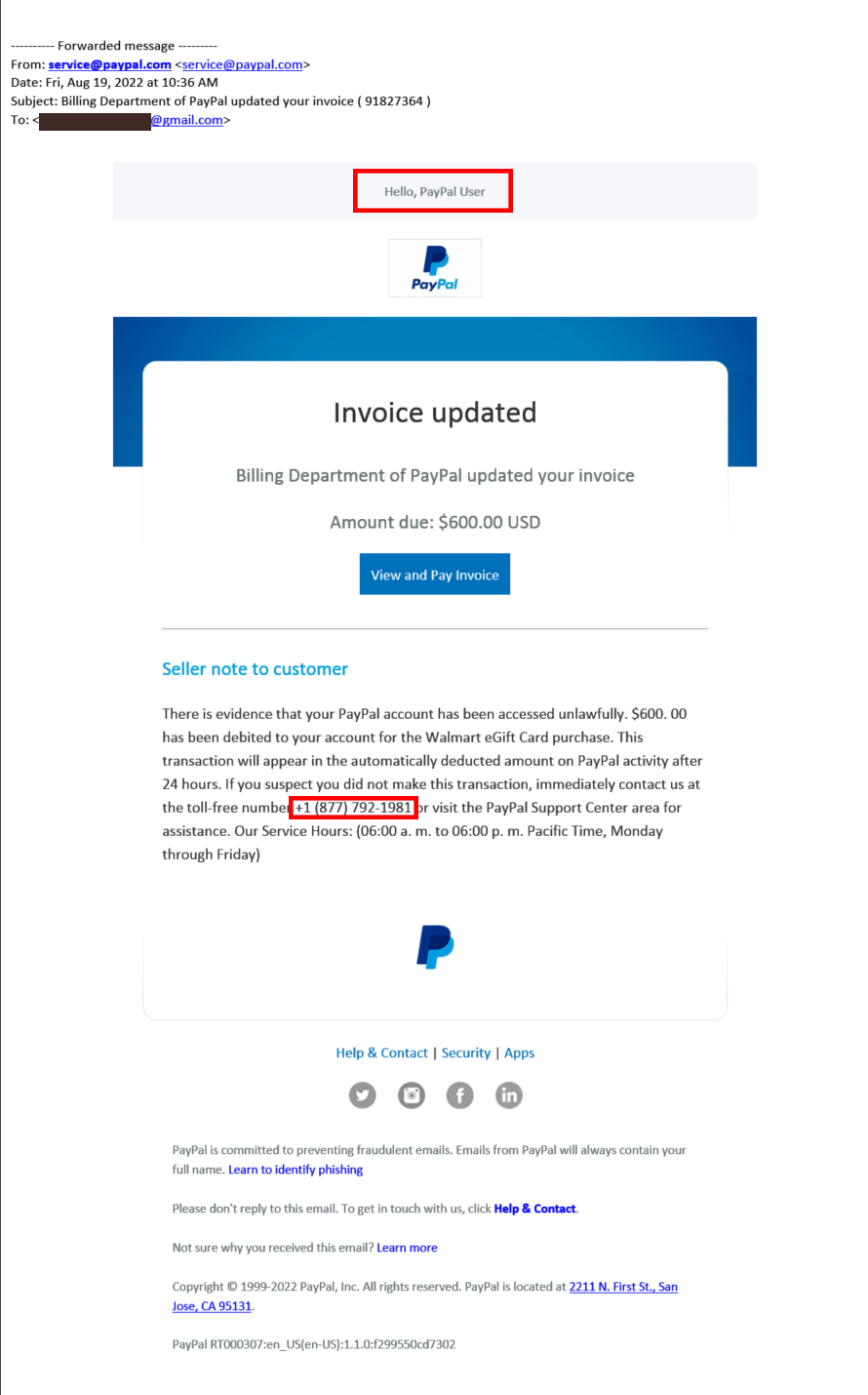
A copy of the phishing e-mail message notifying the user of the PayPal.com invoice.
Note the red outlined user name – if this was real it would have your actual PayPal username. The phone number outlined is from a known scammer call center whose caller ID is “National Grid”. When you see this name on your caller ID, don’t answer the call and block it.
Also, the email headers in the phishing message (See bottom of article) show that it passed all email validation checks as being sent by PayPal, and that it was sent through an Internet address assigned to PayPal, indicating it was sent from a hijacked PayPal user account. Both the email and the invoice state that “there is evidence that your PayPal account has been accessed unlawfully.” This is meant to get your attention. Likely it is someone else’s account that was hacked. (That is not to say yours wasn’t.) To prevent this turn on Multi Factor Authentication in your account (more on that in my next article). The message continues:
“$600.00 has been debited to your account for the Walmart Gift Card purchase. This transaction will appear in the automatically deducted amount on PayPal activity after 24 hours. If you suspect you did not make this transaction, immediately contact us at the toll-free number….”
Here’s the invoice that popped up when the “View and Pay Invoice” button was clicked: (Don’t try this at home if you don’t have the protections I have – which most likely you do not – and don’t call the number) This is what you will see when you click on the “View and Pay” button. in your account.
The phishing message in the invoice is a bit grammatically incorrect (though better than most), the obvious misspelling of “dprt” is a tip-off, although barely noticeable. Having said that, there are many convincing aspects of this hybrid scam. For starters, all of the links in the email lead to paypal.com. Hovering over the “View and Pay Invoice” button shows the button indeed wants to load an actual link at paypal.com, and clicking that link indeed brings up an active invoice at paypal.com.
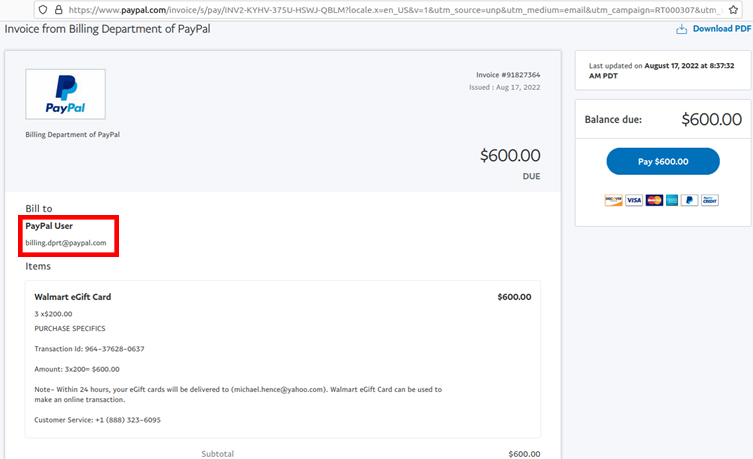
The phony PayPal invoice, which was sent and hosted by PayPal.com. Note the red box shows “PayPal User” and misspelled fake email – “[email protected]”. This should show your PayPal user ID and email address.
Aside from the many readers who have sent me copies. This is just one that was forwarded to me by a TLS reader. I don’t recommend logging into your PayPal account, but if you do, you will find no signs of the invoice in question.
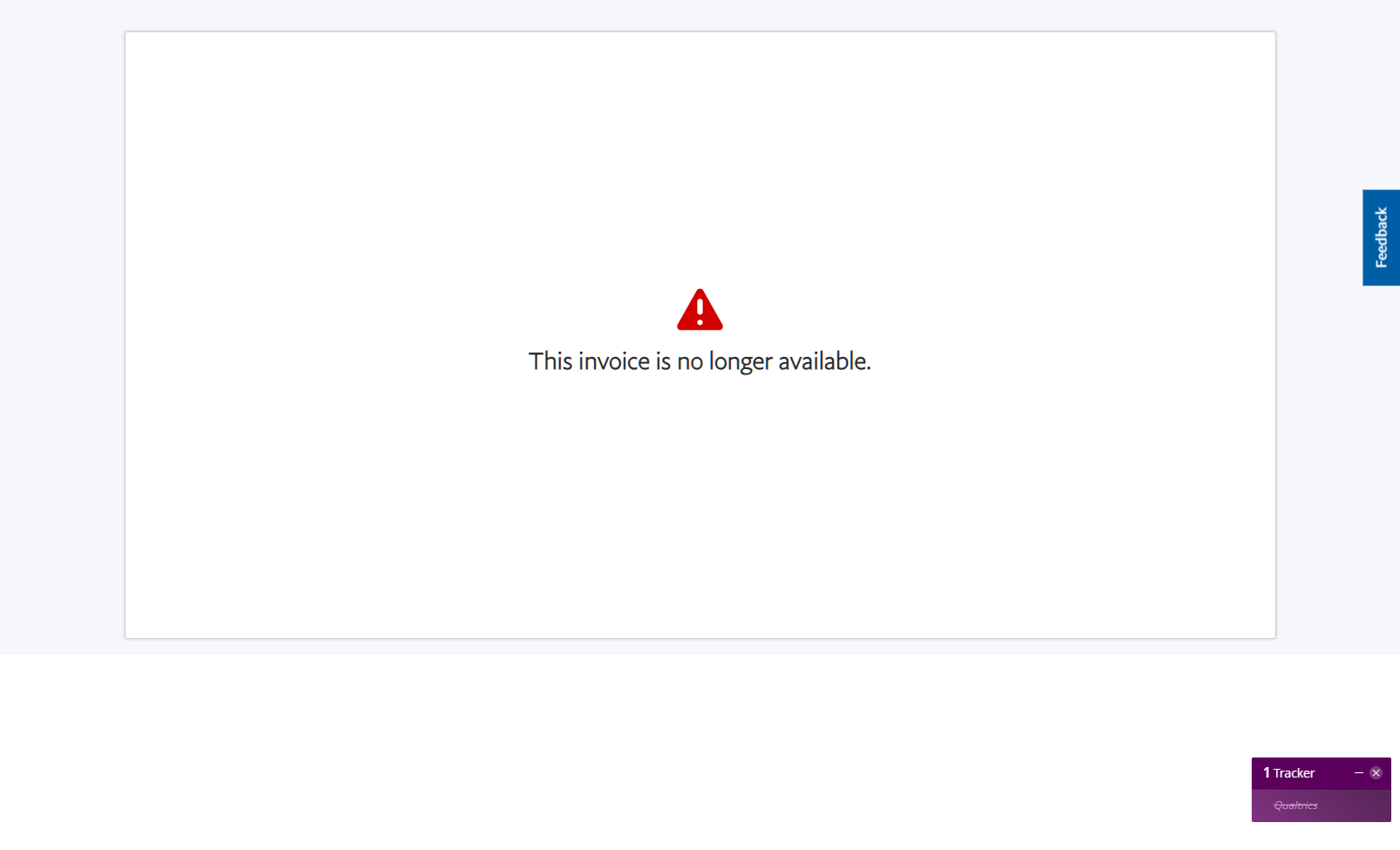
There is no invoice in your account! They want you to call the bogus “customer service” number and follow the instructions.
The email itself is not going to cause any harm but following the instructions given over the phone by going to that link will brick your computer with ransomware.
If you call the toll-free number listed in the invoice someone will answer the phone saying “customer service.” They don’t even try to spoof PayPal or Walmart. Just “customer service.” Almost immediately the person tells you to go globalquicksupport[.]com to download a remote administration tool which will take over your computer. Need I say more?
From the feedback I’m getting, this scam is fooling a tremendous amount of people, since both the email and invoice are sent through PayPal’s systems which guarantees that the message will be successfully delivered. The invoices also appear to have been sent from a compromised or fraudulent PayPal Business account, which allows users to send invoices like the one shown above that looks completely legit.
Once the reader notified me of the scam, I forwarded it to PayPal at ([email protected]). I suggest you do the same.
PayPal said in a written statement that phishing attempts are common and can take many forms.
“We have a zero-tolerance policy on our platform for attempted fraudulent activity, and our teams work tirelessly to protect our customers,” PayPal said. “We are aware of this well-known phishing scam and have put additional controls in place to mitigate this specific incident. Nonetheless, we encourage customers to always be vigilant online and to contact Customer Service directly if they suspect they are a target of a scam.”
In my next article I will show you how to prevent your login and password from getting hijacked so you’re not the one sending out fake invoices or anything else, without your knowledge.
For any coders reading this, here is some of the email header which is totally legit: (scroll down to see the highlighted text)
Delivered-To: redacted
Received: by 2002:a05:6512:200a:0:0:0:0 with SMTP id a10csp1224595lfb;
Fri, 19 Aug 2022 10:36:41 -0500 (EDT)
X-Google-Smtp-Source: AA6agR6sKdnBgXCTyPRdhqx+
+K7DlDYCN8xT7Wqi8oZm195OJ2f6wYLM9wbxeUKhajifkCVLgiTS
X-Received: by 2002:a17:90b:1241:b0:1f3:1d9f:a933 with SMTP id
gx1-20020a17090b124100b001f31d9fa933mr3936447pjb.221.1660746296510;
Fri, 19 Aug 2022 10:36:41 -0500 (EDT)
ARC-Seal: i=1; a=rsa-sha256; t=1660746296; cv=none;
d=google.com; s=arc-20160816;
b=FSLgf+N1ET3mWC9M9Qi9g8CPefVWy6wyWZz/
6A1DV2/4XllZcr2H04CWwlu2paDOge
RJ1AvWMEM4I/
VG4jG2q8MVp3Mpy4wHmsJytyb0fBguVABTSUUXlhGurUY5aeG8qCSeaO
Kgbrtzetf9h526YnEpeoaIxnsTzQVAuNn5uLt+yFKnFfJe5nT3ue3BeeJ3LWrLKokc1+
xuT93EyMxAZLQ7U1qDDPWlhwoNRY2otEzaild1opvBa/
AZidquPq6VC9kvLBgKp2mWY9
l8qKzDHvC1cvL5UlKEjHD9vbKuUnKBJlvnqo2FwbKK577MvjfQOR+8U1XQ0k1ak7Oru7
/G0A==
ARC-Message-Signature: i=1; a=rsa-sha256; c=relaxed/relaxed;
d=google.com; s=arc-20160816;
h=amq-delivery-message-id:mime-version:from:to:subject
:pp-correlation-id:message-id:date:content-transfer-encoding
:dkim-signature;
bh=PbyE+g6+HjhZagjo+V01vCiaM5z3IQYejFCUCoXNLPQ=;
b=pLtZzE6vgXvG90YIt/08XjW8+xXkm1obt5KrvsaDexkJIRm/
R1RzMpXMU+xbYVxFr/
QZJJzw6XC2J0HX8KYHDjlbjWvUvpP27bCqhQiNm9OF7LKlz6Xr+XFlH/++L9/
zdBuy2I
MkkmYM5qtGc1LpksMGXfwnDj4LkVIF62Pp5Lu7TVKVRQ1wMZu3tAPAawplK29V3P3AWN
34SPwbgJYX4QWXhdgcSfu7dwN6JedXR4f74o78IiDtaHKDpG3Wd6gdDU78cNI0qZul+7
giREjrd7k4TB1ZfZ32FzOJugFK+PMldCyDSSoj+73XB5U6xPIQimwxaYkXjflujIu6gk
/kYg==
ARC-Authentication-Results: i=1; mx.google.com;
dkim=pass [email protected] header.s=pp-dkim1
header.b=l2+AbSdp;
spf=pass (google.com: domain of [email protected] designates
173.0.84.225 as permitted sender) [email protected];
dmarc=pass (p=REJECT sp=REJECT dis=NONE) header.from=paypal.com
Return-Path: [email protected]
Received: from mx0.slc.paypal.com (mx0.slc.paypal.com. [173.0.84.225])
by mx.google.com with ESMTPS id
d13-20020a170902cecd00b00172549e3acfsi1497284plg.175.2022.08.17.07.24.
56
for <redacted>
(version=TLS1_2 cipher=ECDHE-ECDSA-AES128-GCM-SHA256
bits=128/128);
Fri, 19 Aug, 2022 10:36:41 -0500 (EDT)
Received-SPF: pass (google.com: domain of [email protected]
designates 173.0.84.225 as permitted sender) client-ip=173.0.84.225;
Authentication-Results: mx.google.com;
dkim=pass [email protected] header.s=pp-dkim1
header.b=l2+AbSdp;
spf=pass (google.com: domain of [email protected] designates
173.0.84.225 as permitted sender) [email protected];
dmarc=pass (p=REJECT sp=REJECT dis=NONE) header.from=paypal.com
DKIM-Signature: v=1; a=rsa-sha256; d=paypal.com; s=pp-dkim1;
(Etc., ………………………….)


yes. I recently got such a phony email and immediately reported it back to PayPal. One red flag was that the email itself wrote that’s Paypal will always use the account holders name in any address and the email was to addressed to PayPal User . So it seems as if the scammer was either careless or did not read English.
Thank you for this! I saw them. Got worried. Glad my hunch that it was a scam is correct! They are definitely getting more advanced as time goes on!