 By Ron Benvenisti. Welcome to part one of my four part series entitled ”Network Security for Dummies!” This series will teach business owners what the basics are for arming themselves against the ever-present information security threats and risks that are crouching at the door, or the backdoor, as it were.
By Ron Benvenisti. Welcome to part one of my four part series entitled ”Network Security for Dummies!” This series will teach business owners what the basics are for arming themselves against the ever-present information security threats and risks that are crouching at the door, or the backdoor, as it were.
There are really just two simple rules to follow:
Keep your system and network configured correctly. (Since rule Number 1 is almost impossible achieve 100% ), you also need to:
Know what’s coming into and going out of your network.
By following these rules you will be able to detect if and when something dangerous, privacy breach or when a costly loss is taking place. These basic rules actually need just three basic tasks which I call the ABC’s of Network Security:
Protection: Derived from Rule #1. Configure your system and network as correctly as possible.
Detection: Derived from Rule #2. Knowing when the configuration has changed or some network activity shows there’s a problem.
Reaction: Derived from task B. Respond quickly to the problem and get to a safe and stable state ASAP.
Now if you’re thinking to yourself, “Well I’m just a small potato, a mom and pop operation, this doesn’t apply to my business and even if it did what do I have to lose?” I would suggest that you just failed to comprehend your very first lesson. I can understand that, not because it doesn’t apply to you, but…
Achieving a perfect security score of 100 is almost impossible but to be responsible to our business and more importantly to our families and customers who depend on us everyday we have to acknowledge and accept a certain level of risk and realize that at least a 90 is possible and is absolutely necessary to shoot for. But most businesses don’t consider that risk, as defined here: the likelihood of a real and costly threat.
Businesses owners and financial officers of all stripes from small potatoes to big fish to 800 pound gorilla corporations are generally uninformed or simply in denial of what the real vulnerabilities to their businesses are. It’s not just because they may be playing ostrich with their heads in the sand, or perceiving security as an expense that impacts the bottom line, rather than an insurance policy against a tragic loss. Why is that? It’s simply because risk is hard to calculate.
But the only way to get any idea about the serious damage that can be done is by honestly considering your exposure, and the exploitable vulnerabilities that you likely already have. And every business has them. What they are and how to beat them will be presented in Part 2.
Congratulations, if you stuck with me this far, you are already 25% less of a Network Security dummy!

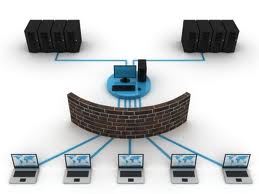
Now if i could only understand what was said here!