 New Jersey Targeted to Steal Microsoft Account Credentials
New Jersey Targeted to Steal Microsoft Account Credentials
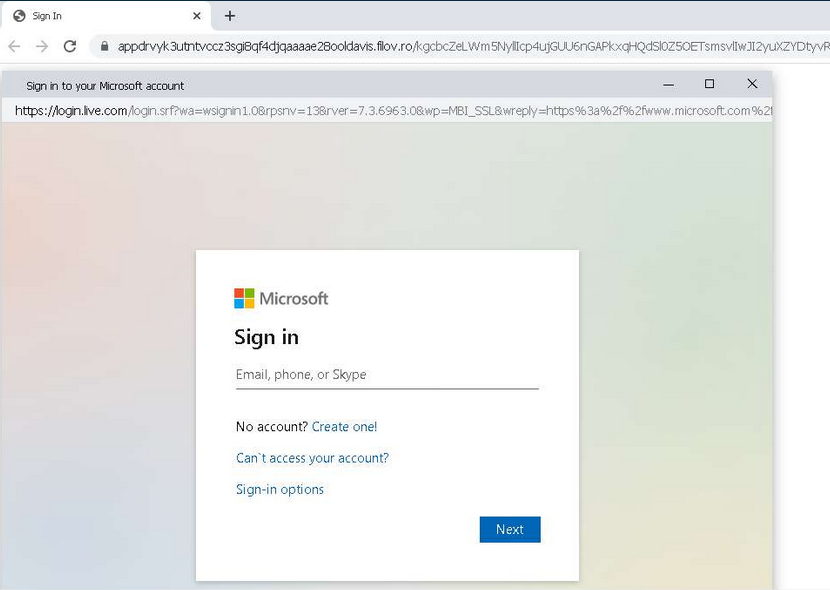
A new technique known as a Browser-in-the-Browser (BitB) attack is being used to socially engineer users into entering account credentials within phishing websites. This technique exploits third-party single sign-on (SSO) options embedded in websites, typically displayed as “Sign in with..” In legitimate circumstances, the user is presented with a pop-up window to log in.
In BitB attacks, a user is redirected to a fraudulent browser window created by the threat actors, which displays an official website domain in attempts to convince the user that the authentication request is legitimate. Once the user submits their credentials, they are sent to the threat actors behind the scheme. This technique has been used in attempts to convince New Jersey State employees to provide their Microsoft account credentials.
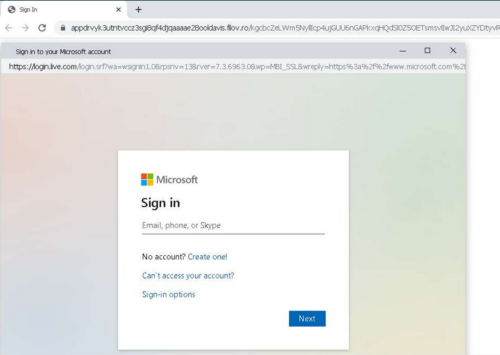
Users are advised to refrain from submitting account credentials into websites and forms navigated to via links provided in emails, particularly those from unknown or unverified senders. In addition, users are encouraged to enable MFA (Multi Factor Authentication) on all accounts to prevent account compromise because of credential theft or exposure.
Uptick In Russia/Ukraine Cyber Threats
Indications of a significant risk due to increased hacking, virus, or other malicious activity that compromises systems or diminishes service originating or being routed through Ukraine have been observed.
Note: The language used here is, “routed through Ukraine.” This is not a definitive proof that cyberattacks are originating in Ukraine. They can appear that way because of basically juvenile techniques to spoof IP addresses so that the final egress point appears to be Ukraine.
 The United States Defense Intelligence Agency has an extremely robust and secure connection with Ukrainian intelligence.
The United States Defense Intelligence Agency has an extremely robust and secure connection with Ukrainian intelligence.
A continuously growing number of threat actors are using the war as a lure in phishing and malware campaigns. Government-backed actors from China, Iran, North Korea and Russia, as well as various unattributed groups, have used various Ukraine war-related themes in an effort to get targets to open malicious emails or click malicious links.
Financially motivated and criminal actors are also using current events as a means for targeting users. One threat actor is impersonating military personnel to extort money for rescuing relatives in Ukraine. Multiple ransomware brokers are continuing to operate in a business-as-usual sense.
China’s PLA SSF, has conducted offensive and retaliatory campaigns against government and military organizations in Ukraine.
Phishing Campaigns Targeting US
Russian-based threat actors have launched credential phishing campaigns, targeting several US based NGOs and think tanks, the military of a Balkans country, and a Ukraine based defense contractor. However, for the first time, They have begun to target the military of multiple Eastern European countries, as well as a NATO Centre of Excellence. These campaigns were sent using newly created Gmail accounts to non-Google accounts, so the success rate of these campaigns is unknown.
Cash App
Block Inc. confirmed a data breach affecting roughly 8.2 million current and former US Cash App customers. A Form 8-K SEC was filed with the US Securities and Exchange Commission on April 4, detailing that a former employee without authorization accessed and downloaded records containing customer information on December 10. Breached information includes full name and brokerage account number and, for some customers, brokerage portfolio value, holdings, or specific stock trading activity. Block Inc. stated in the filing that other sensitive information, such as personally identifiable information and account credentials, were not exposed in the data breach. The intent behind the data breach is unknown at this time. Upon discovery of the breach, Block Inc. notified law enforcement, launched an investigation with a forensics firm, and took steps to remediate the incident. The company will notify affected customers of the breach’s potential impact.
Mailchimp Breach Leads to Attempted Crypto Theft Evading US sanctions
Mailchimp, an email marketing firm, confirmed that a threat actor breached the popular email marketing app’s internal customer support and account management tools by acquiring Mailchimp employee credentials via a successful social engineering attack. The threat actor gained access to 319 Mailchimp accounts and pilfered customer data that was later used in a targeted phishing campaign against cryptocurrency and finance industries. The threat actor may have also gained access to API keys for an unspecified number of customers, which have since been disabled. Wallet owners received phishing emails of an alleged data breach notification that instructs the recipient to “download the latest version” of the software. The link sends the recipient to a phishing site that prompts the user to connect their wallet and enter their recovery seed, which is used to regain wallet access in the event a device is lost or stolen. The threat actor is then able to transfer funds to a wallet under their control. Decentraland also confirmed that its newsletter subscribers’ email addresses were compromised in the Mailchimp breach. At this time, it is uncertain how many other cryptocurrency services or financial institutions are affected. The increased targeting of cryptocurrency and financial institutions will likely continue, in part because cryptocurrency could be used to evade US sanctions.
AcidRain Wiper Deployed Against Satellite Modems in Ukraine
A wiper (data-destroying) malware dubbed AcidRain. is designed to wipe modems and routers performs an in-depth wipe of filesystem and storage device files. If running as a root user, the malware can overwrite and delete nonstandard files in the filesystem. Once the system is wiped, the device reboots and is rendered inoperable. It is not clear if this has affected systems donated to Ukraine by Elon Musk to facilitate rescue efforts.
Users should refrain from responding to unsolicited communications, clicking links, and opening attachments from unknown senders and exercise caution with communications even from known senders.
If you are unsure of a message’s legitimacy, contact the sender via a separate means of communication – such as by phone – before taking any action. Keep systems up to date and implement security controls that help prevent account compromise, including establishing strong passwords, enabling Multi Factor Authentication where available. Be advised that SMS text-based apps are also affected.

Is my connection slow or is this place slow for everyone else?