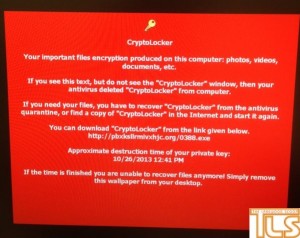
 PHOTO: A Lakewood resident tells TLS he was hit with a malware which is demanding ransom money before his encrypted files can be released back to him.
PHOTO: A Lakewood resident tells TLS he was hit with a malware which is demanding ransom money before his encrypted files can be released back to him.
The man tells TLS he received an innocent looking email this morning which appeared to be a voicemail, but when he opened it, his computer became infected by his documents becoming encrypted.
It turns out, the malware he was hit with is a relatively new malware going around called CryptoLocker – a type of Ransomware. And the hackers mean business. If their demands to pay them a ransom of $300 – via an untraceable venue – aren’t met, the computer files remain encrypted, making them inaccessible.
And there’s a deadline too – you have 100 hours to make the payment or the ‘key’ to unlock your files is thrown away.
According to reports about CryptoLocker, the malware can also be spread through phony emails designed to look like they’re from legitimate businesses.
After encrypting your files, the window about the 100 hour countdown opens up and provides you with details on how to pay the ransom.
Though security companies are reportedly working on preventing this serious threat, the user tells TLS he brought his computer to several technicians in Lakewood who said they were unable to get around it. A technician also noted that according to his research on the issue, most users did not get their files back after paying the ransom money.
Users are encouraged to remain vigilant when opening emails which may look suspicious. [TLS]

A Professional technician would be able to get around these issues since this type of Malware has existed for years. This is not some new age virus that no one has seen before. It’s extremely popular in Russia and prays on less experienced users.
Try someone with a degree next time, or, prevent it by practicing better computer habits. Viruses and Malware all have one thing in common, user error.
I’ve had lots of experience with this virus and worked on this with some data recovery experts around the world, at this time we don’t have a solution to recover the data or get past the encryption. I’ve had 5 – 10 cases in the past few weeks and in those cases the people that felt the data was worth the money and paid for it did in fact get the drive decrypted and restored all their files. If anyone does that I do recommend taking measures to insure it doesn’t come right back for example wiping and reinstalling their hard drive. If you need any more advice feel free to contact me.
I had a similar issue today as well. I filled out a health questionnaire on my laptop for a doctor’s office. I pressed submit and the doctors form cleared and the screen said that the time limit expired and deleted my info. I worked on it straight for 15 minutes since it had a lot of details and questions so that couldn’t be. The doctor office said this never happened to anyone and they did not get my info. A second after that screen came up, I got a phone call from private name, private #. I decided to pick it up and it was “someone from Microsoft” saying that I had a virus and would I like them to fix it! The guy sounded like he was from India with a lot of noise in the background. I hung up on him. Later a police cruiser drove past me and I called it down and mentioned the story and the police woman said this is going around and she is glad that I didn’t fall for it. If you agree to have them fix it, (as per police) then they implant a virus in your computer and take all of your important private information out with it and charge you as well $$$. Be aware!!
I received a phone call from some indian soundding native with a lot of noise in the background telling me about the problems with my computer and for $99 he can fix it. He even took me to some site which I don’t know if its a real microsoft site and if he is even affiliated.
Of course, I hung up on him after telling him he’s a scam.
Don’t store important documents in “my documents folder” create a different folder to keep them and back them up on a flash drive.
Wow. This is scary.
And the fact that DH Data recovery says its irrecoverable doesnt make it any less frightening. :{
Hes a professional data recovery expert with many years of experience in the field.
What is the contact info to DH Data Recovery?
Yuri can get it out
It seems the only way to be safe is to have all your files backed up (Google Drive, Skydrive Etc.).
A very large company 3weeks ago that had this and it encrypted all files in their share on their server and lucky thing they use our offsite backup and fixed all very quickly
And there is no simple fix without a backup or paying ransom – not recommended
There is a thorough post on the Snopes website about this virus. It is real, and there is no fix known as of now, besides for paying the ransom money.
The very large company caught the virus on Thursady night. The technician first came on Monday. They lost two days of work.
1. I’m glad you agree you don’t have the experience. I can send you the link to do it to your computer and when you find that technician let me know.
2. Thanks for popping in. We need people to know about this so they don’t lose their data. I have heard conflicting reports on the ransom part decrypting the files, but at this point I believe that this variant does actually decrypt the file when one pays them.
5. Doesn’t help this particular virus will infect all connected drives. Including network drives and flash drives. It searches for the file types it infects all the whole drive not just My Documents. It also infects skydrive and google drive.
9. I was busy today with a skydrive that got infected. While it hadn’t yet had a chance to sync up so the user was able to recover 95% of his files from another PC logging into his skydrive account. It did infect his sky drive. The only thing that helps is a restore from a good backup. Which means backups that are on a connected drive (USB etc) could technically also get encrypted and hence worthless. Offsite or offline backup would be the only one that is protected from this.
This isn’t a virus that comes with a call from Microsoft or something it’s way more complicated than that, all you’re data is heavily encrypted. Storing the files somewhere other than my documents doesn’t either help as they encrypt by file extension, meaning it will automatically encrypt all pictures, documents etc.
I can be reached at 718.509.9211
Important Note –
I think that there is an error in this post. In today’s internet day and age, information isn’t hard to put out there and isn’t hard for people to find. So, if you do just a little research, this CryptoLocker seems to be “honest” to their word of fixing the issues once the fee is paid. Not that I’d call them honest, but it does seem that people get their money.
I’m unsure where “technicians in Lakewood” get their information from, but in this case they seem to be severely incorrect. You can see the links below showing that to the best of information that’s out there, they are restoring peoples computers once it’s paid.
I used HitmanPro and it worked wonders to remove the virus.
DH is one of the biggest data restoration experts in the tri-state area. He’s the only guy I trust.
@ Kiddishman – This isn’t the fake FBI, NSA, CIA Virus – this Virus actually goes ahead and physically encrypts your drive. It leaves most of the OS data intact but searches your entire drive and encrypts all user data i.e. Documents, Pictures, Quickbooks data etc.
In the older versions of this virus we sometimes had luck recovering the encryption key and recovering the data, they since got smarter and use secure delete to erase the key making it impossible to recover and figure out the encryption code.
The only way to recover this data – at this time is by getting the key, the only way to get the key is by paying the money. In the older version of this virus they had an email address that you can communicate with them – they have since removed that as well. We tried tracing the email address 2 years ago when we were working on the earlier version of the virus and it led us to Germany and we couldn’t get any help from the authorities there.
The key is to be very careful opening emails, make sure you have a good firewall in place and secure RDP ports and any other typical ports.
Guys, listen to DH. He knows his stuff.
Public shout-out for previous tech help.
Thanx
Back everything up, and then it doesn’t matter.
Backup won’t help if it infects your backup as well, or replaces the backed up data with these encrypted files.
You can sometimes recover the files by using either Shadow copy or restoring previous versions of the files